Hi, sorry, let me start from scratch
I have this report
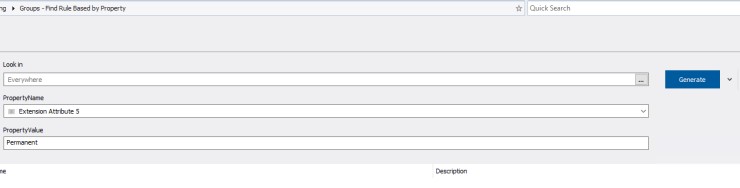
Parameters
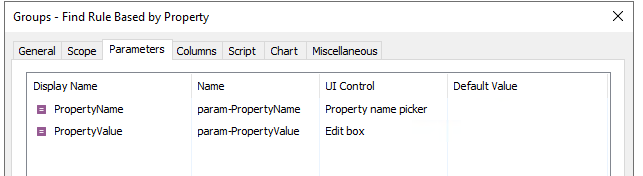
Script
$propertyName = "%param-PropertyName%"
$propertyValue = "%param-PropertyValue%"
try
{
$groupCriteria = New-AdmCriteria -Type "group" -Expression {membershipType -eq "rule-based"}
$Context.DirectorySearcher.AddCriteria($groupCriteria)
$criteriaToCompare = New-AdmCriteria -Expression {$propertyName -eq $propertyValue}
$criteriaJsonToCompare = $criteriaToCompare.Item("*").Items.ToJson($null)
$searchResultIterator = $Context.DirectorySearcher.ExecuteSearch()
while ($Context.MoveNext($searchResultIterator))
{
$searchResult = $searchResultIterator.Current
$group = $Context.BindToObjectBySearchResult($searchResult)
foreach ($rule in $group.MembershipRules)
{
if ($rule.Type -ne "ADM_BUSINESSUNITMEMBERSHIPTYPE_QUERY")
{
continue
}
$criteria = $rule.GetCriteria()
if ($criteria.ToJson($NULL) | Select-String -Pattern $criteriaJsonToCompare -SimpleMatch)
{
$Context.Items.Add($searchResult)
break
}
}
}
}
finally
{
if ($searchResultIterator)
{
$searchResultIterator.Dispose()
}
}
If I run the report, I get only one rule based group

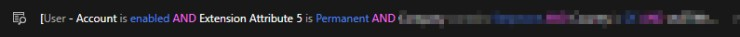
This group has the following rule
But, we have also some other rule based groups like with this rule
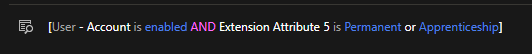
This group is not found by the report/script.
Is there any chance to find also groups with the rule set of the second one?
My goal is: Find all rule base groups where the condition contains
extensionAttribute5 is Permanent
However we need also to find groups with rule
extensionAttribute5 is Permanent OR X OR Y