Hello,
Yes, it is possible to implement your scenario using Adaxes.
-
Define two Custom Commands for adding and removing users to/from groups. The commands will add/remove the account of the initiator to/from the selected distribution list.
When creating Custom Commands, on the 2nd step of the wizard, select the Group object type.
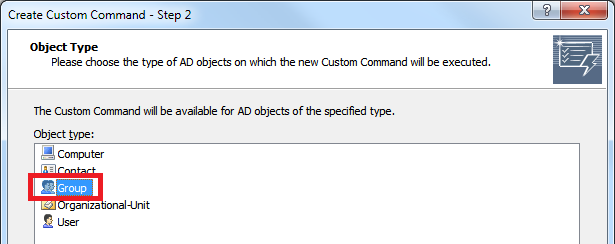
On the 3rd step of the wizard, click the Add Action link and select the Run a program or PowerShell script action.
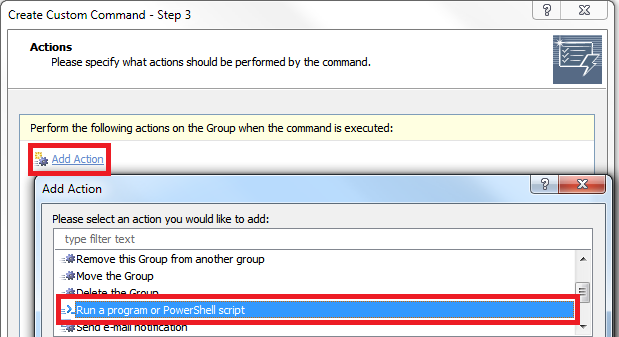
Use the following scripts to add/remove the initiator to/from groups:
Add to Group
$Context.TargetObject.Add("Adaxes://%adm-InitiatorDN%")
Remove from Group
$Context.TargetObject.Remove("Adaxes://%adm-InitiatorDN%")
-
Grant permissions to users to execute the two Custom Commands for the groups located in a specific OU. For more details, see Grant Rights to Execute Custom Commands.
-
Configure the Home Page of the Web Interface. For more details, see Configure Home Page Actions.
Define a Home Page action to execute the Add to Distribution List command you created on the first step.
- On the Target Object Selection step, enable the Allow selecting only AD objects located under a specific OU or container option, and specify the DN (Distinguished Name) of the OU where groups are located. To get the DN of an AD object, right click it in Administration Console, open the submenu of the Copy item, and select Copy DN.
- Enable the Allow selecting only AD objects that match the specific LDAP filter option and enter the following LDAP filter: (!(member=%adm-InitiatorDN%))
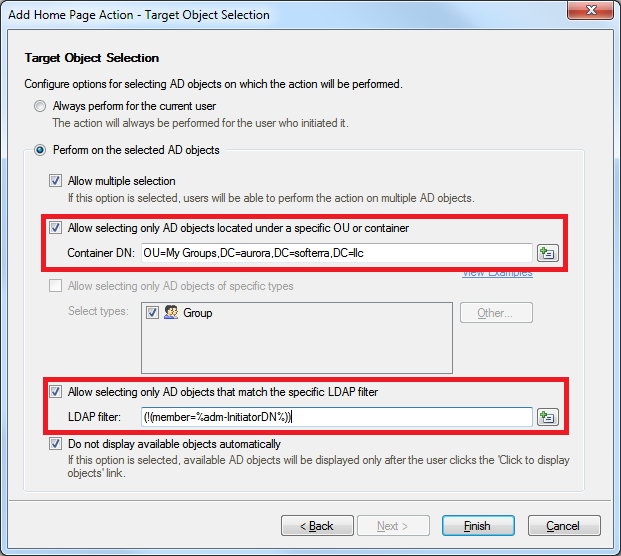
Define a Home Page action to execute the Remove from Distribution List command you created on the first step. Apply the same options for the action, and specify the following LDAP filter: (member=%adm-InitiatorDN%)
Define a Home page action to allow users to view the groups they are member of.
- Select the View User action and click Next.
- On the Object Selection step, select the Always view properties of the currently logged on user option.
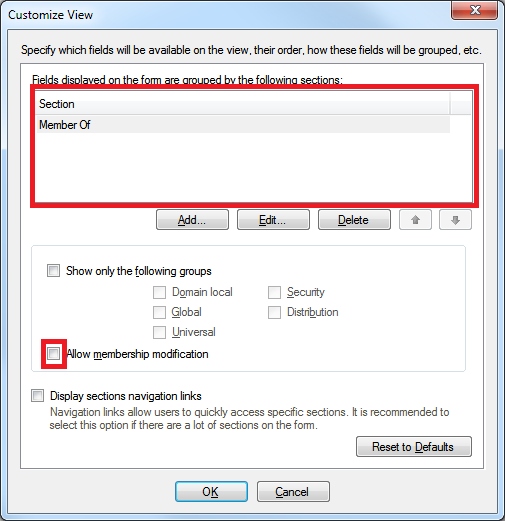
- On the View Customization step, enable the Use customized view option and click Customize View.
- Customize the view to display only the Member Of section. For details, see Customize Forms for User Creation and Editing.
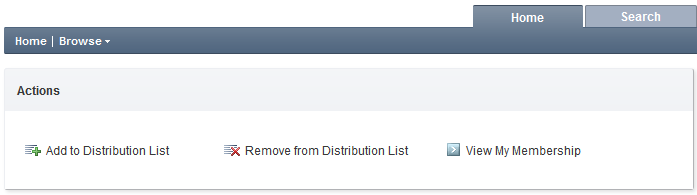
At the end, the Home page of the Web Interface will look like this: