We managed to identify the cause of the issue. The thing is that when the User cannot change password Account Option is set for a user, the user's ACL is built incorrectly. This is a bug in Adaxes that will be fixed in the next release, thank you for the bugreport!
To fix the issue until a fix is available, you can use the following script that will regenerate the ACL:
$ADS_RIGHT_DS_CONTROL_ACCESS = 0x100
$UserChangePasswordRightGuid = "{ab721a53-1e2f-11d0-9819-00aa0040529b}"
function MoveDenyAce($dacl, $trusteeType)
{
for ($i = 0; $i -lt $dacl.Count; $i++)
{
$ace = $dacl[$i];
if (($ace.AceFlags -band [System.Security.AccessControl.AceFlags]::Inherited) -ne 0)
{
continue
}
if (($ace.AccessMask -ne $ADS_RIGHT_DS_CONTROL_ACCESS) -or
($ace.ObjectAceType -ne $UserChangePasswordRightGuid))
{
continue
}
if ($ace.AceQualifier -ne 'AccessDenied')
{
continue
}
if (-not $ace.SecurityIdentifier.IsWellKnown($trusteeType))
{
continue;
}
$dacl.RemoveAce($i);
$dacl.InsertAce(0, $ace)
}
}
$Context.TargetObject.GetInfoEx(@("ntSecurityDescriptor"), 0)
$securityDescriptorPropertyEntry = $Context.TargetObject.GetPropertyItem("ntSecurityDescriptor", "ADSTYPE_OCTET_STRING")
$securityDescriptorBinary = $securityDescriptorPropertyEntry.Values[0].OctetString
$rawSecurityDescriptor = New-Object "System.Security.AccessControl.RawSecurityDescriptor" @($securityDescriptorBinary, 0)
$dacl = $rawSecurityDescriptor.DiscretionaryAcl
MoveDenyAce $dacl 'SelfSid'
MoveDenyAce $dacl 'WorldSid'
$rawSecurityDescriptor.DiscretionaryAcl = $dacl
$securityDescriptorBinary = new-object byte[] $rawSecurityDescriptor.BinaryLength
$rawSecurityDescriptor.GetBinaryForm($securityDescriptorBinary, 0)
$Context.TargetObject.Put("ntSecurityDescriptor", $securityDescriptorBinary)
$Context.TargetObject.SetInfoEx(@("ntSecurityDescriptor"))
You can use Adaxes Business Rules and the Run a program or PowerShell script action to execute the script automatically once the User cannot change password Option is set. For example, if you set the User cannot change password in a Business Rule, you can insert the Run a program or PowerShell script action that will execute the above script after setting the User cannot change password Account Option. To do this:
- Launch Adaxes Administration Console.
- In the Console Tree, navigate to and select the Business Rule that sets the User cannot change password Account Option.
- Select the set of actions and conditions that sets the User cannot change password Account Option and click the Add Action button.
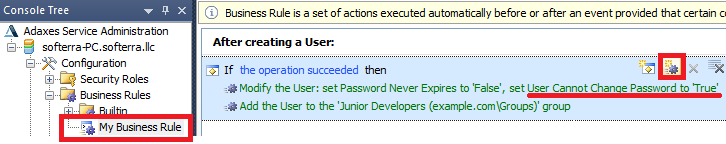
- Select the Run a program or PowerShell script action and paste the above script.
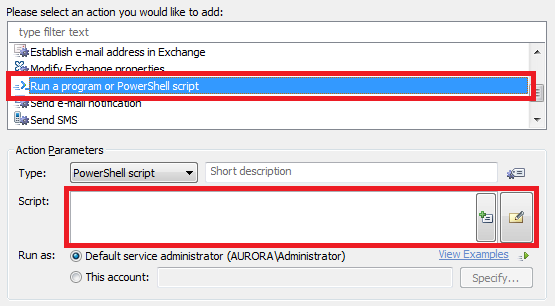
- Click OK.
- Use the arrow buttons at the bottom of the actions and conditions of the Business Rule to place the newly create action right after the User cannot change password Account Option is set.
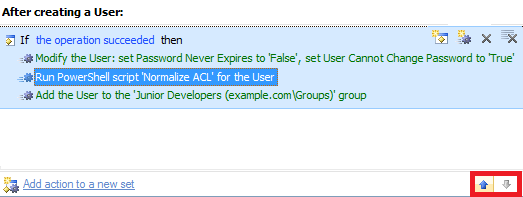
- When done, save the Business Rule.
Alternatively, if the Account Option is set creating a new user, you can create a Business Rule that will launch the above script right after creating a new user in AD. to do this:
- Create a new Business Rule.
- On the 2nd step of the Create Business Rule wizard, select User and After Creating a User.
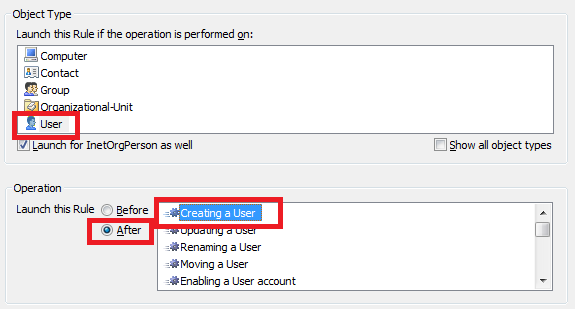
- on the 3rd step, add the Run a program or PowerShell script action and paste the above script.

- Click OK.
- Click the Add Condition button.
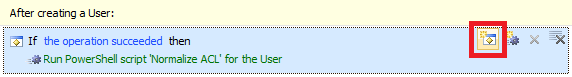
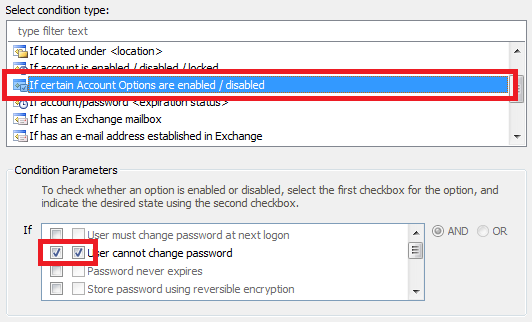
- Select the If certain Account Options are enabled/disabled condition type.
- Check the two checkboxes opposite the User cannot change password option.
- Finish creation of the Business Rule.