Thank you for clarifying. Here is the script for the new custom command. In the script:
- $memberDNsParameterName – specifies the name of the AD object picker parameter.
- $separator – specifies the separator character for multiple values of AD object picker.
- $pipelined – specifies whether the membership update should be performed via Adaxes pipeline i.e. if set to $True, all applicable business rules will trigger after adding a member to a group, log records for adding group members will be created, etc.
$memberDNsParameterName = "param-members" # TODO: modify me
$separator = ";" # TODO: modify me
$pipelined = $True # TODO: modify me
# Get parameter value
$memberDNsParameterValue = $Context.GetParameterValue($memberDNsParameterName)
$memberDNs = $memberDNsParameterValue.Split($separator)
# Get target group type
$targetGroup = $Context.BindToObjectEx($Context.TargetObject.AdsPath, $pipelined)
$targetGroupType = $targetGroup.Get("groupType")
$isTargetGroupGlobal = $targetGroupType -band [Softerra.Adaxes.Interop.Adsi.ADS_GROUP_TYPE_ENUM]::ADS_GROUP_TYPE_GLOBAL_GROUP
$targetGroupSecurityEnabled = $targetGroupType -band [Softerra.Adaxes.Interop.Adsi.ADS_GROUP_TYPE_ENUM]::ADS_GROUP_TYPE_SECURITY_ENABLED
$targetGroupDomain = $Context.GetObjectDomain("%distinguishedName%")
# Check if new members contain users from other domains
foreach ($dn in $memberDNs)
{
$memberDomain = $Context.GetObjectDomain($dn)
if ($isTargetGroupGlobal -and
$targetGroupDomain -ne $memberDomain)
{
$targetGroupType = [Softerra.Adaxes.Interop.Adsi.ADS_GROUP_TYPE_ENUM]::ADS_GROUP_TYPE_UNIVERSAL_GROUP -bor $targetGroupSecurityEnabled
$targetGroup.Put("groupType", [Int32]$targetGroupType)
try
{
$targetGroup.SetInfo()
}
catch
{
$Context.LogMessage("An error occured while changing the group type. Error: " + $_.Exception.Message, "Error")
return
}
$isTargetGroupGlobal = $False
}
$path = New-Object Softerra.Adaxes.Adsi.AdsPath $memberDomain, $dn
try
{
$targetGroup.Add($path)
}
catch
{
$Context.LogMessage("An error occured while adding a member. Error: " + $_.Exception.Message, "Error")
}
}
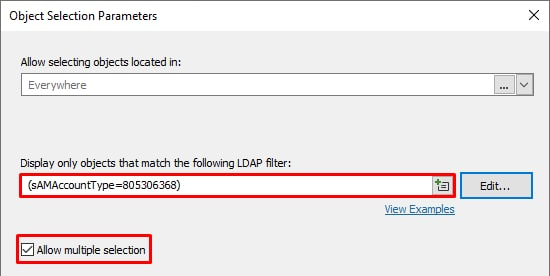
You can configure the custom command exactly as the one before, except you need to specify different object selection settings for the AD object picker parameter so that only users can be selected.
 For your reference, the workflow where you have to change the group scope before adding a member might indicate that there are some issues with how your groups are set up. You might want to review your group structure to avoid such workarounds in the future.
For your reference, the workflow where you have to change the group scope before adding a member might indicate that there are some issues with how your groups are set up. You might want to review your group structure to avoid such workarounds in the future.