Hi,
I will try and set this out a bit clearer as I did not do so properly before.
We have the need to disable inactive accounts after a 60 day period. And also a need to disable accounts that have never logged in after a 60 day period.
We had noticed that even if an account was already disabled the script would still run against them and we dont want that as the email we generate then creates a Jira ticket for User Services to then fully deprovission the account.
o what we have is this:
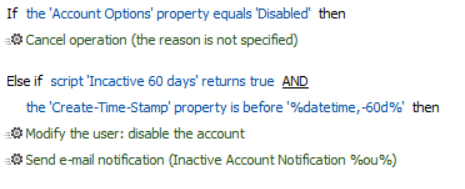
We then ran the above for the 1st time this morning and it disabled 29 accounts, some of which was perfectly fine. But other accounts had Last Logon - Unspecified and Last Login Timestap as a recent date like below:
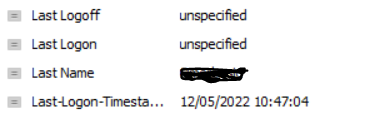
The accounts like this also got disabled, I believe the Unspecified is due to DC replication.
Maybe I am over thinking it and doing it as per the last responce is a better and easier way of achiving our requirements.
Regards