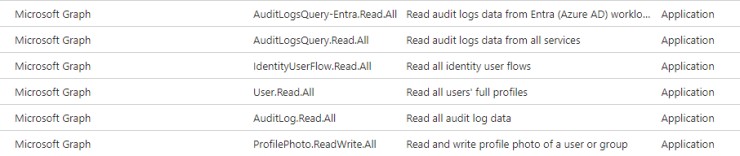
I was able to figure this out and implement it in Adaxes. You'll want to make sure you have these permissions in your enterprise application for Adaxes in Azure. They have to be Application, not Delegated.
Once this is done the last logon timestamp attribute appeared for the Azure users in Adaxes. We created a scheduled task that would scope to the Azure domain users OU, look for the on-prem synced attribute to be true (that way this won't inadvertently target cloud only users), check if account is enabled, check if last-logon-timestamp attribute is before %datetime, -1M% (you can adjust the length of time to your preference), and this one is optional but I added in a When Created attribute is before %datetime, -1M% just so it wouldn't target newhires.
For the action I just had it run a powershell script and did the following:
disable-adaccount -identity %onPremisesObjectGuid% -confirm:$false
Hope this helps!